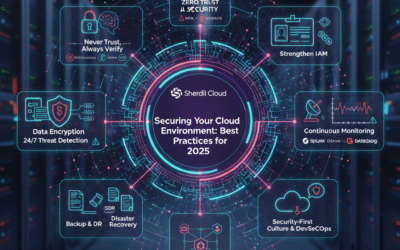
The motto “never trust, always verify” encapsulates the Zero Trust paradigm. In contrast to the conventional perimeter-centric security, which uses firewalls to demarcate “trusted” internal networks from the “untrusted” outside world, Zero Trust does away with the idea of a trusted zone in its entirety.
Each user, device, or application has to establish its authenticity each time it makes a request irrespective of location or prior authentication.
Some of the defining principles of Zero Trust are:
-Authentication of each request: continuously authenticate and authorize devices and users.
-Least privilege access: only provide permissions necessary for a given task.
-Micro-segmentation: segment networks into tiny, well-managed zones to constrain lateral mobility.
-Continuous monitoring: monitor all user activity and system behavior for anomalies.
At Sherdil Cloud, we architect Zero Trust environments for each client’s cloud ecosystem, so security never has to compromise on performance or productivity.
What Is Zero Trust Architecture?
The “never trust, always verify” mantra encapsulates the Zero Trust paradigm. As opposed to the traditional perimeter defense model that depends on firewalls to isolate “trusted” internal networks from the “untrusted” outside world, Zero Trust does away with the idea of a trusted zone entirely.
Each user, device, or application must authenticate itself every time it makes a request without regard to location or past authentication.
Some of the main tenets of Zero Trust are:
-Validation of all requests: constantly authenticate and authorize users and devices.
-Least privilege access: provide only the privileges required to perform an action.
-Micro-segmentation: segment networks into small, controlled segments to restrict lateral movement.
-Continuous monitoring: monitor all user activity and system behavior for anomalies.
At Sherdil Cloud, we architect Zero Trust frameworks tailored to each client’s cloud environment, ensuring security doesn’t come at the cost of performance or productivity.
Why Traditional Security No Longer Works
Historically, organizations used firewalls, VPNs, and endpoint protection for data security. However, the advent of cloud, remote work, and SaaS applications has made corporate boundaries disappear.
The attackers are no longer required to pass through the perimeter, they can leverage compromised credentials, third-party access, or misconfigured cloud resources. They can once inside move laterally to access sensitive information without being detected.
Zero Trust removes this weakness by considering each attempt at access as possibly malicious. Even if a hacker has gained control over one user account, he or she can’t proceed easily further inside the network since each system and move needs separate verification.
The Core Components of Zero Trust
Zero Trust is not a product, it’s a strategic model made up of several layers of security. These are the blocks on which Sherdil Cloud builds for a full-fledged Zero Trust solution:
1.Identity and Access Management (IAM)
Identity is the new perimeter. Robust authentication and role-based access control (RBAC) are the pillars of Zero Trust. Multi-Factor Authentication (MFA), Single Sign-On (SSO), and ongoing behavioral monitoring guarantee only authenticated users access sensitive systems.
2.Device Security and Compliance
All devices corporate or personal (BYOD), need to pass compliance requirements prior to accessing resources. Endpoint detection and response (EDR) tools continuously evaluate device health, software revisions, and security posture.
3.Micro-Segmentation and Network Control
Dividing networks into smaller segments allows organizations to segment workloads and contain breaches. For instance, if an attacker gets access to a web server, micro-segmentation denies them access to the database layer.
4.Data Protection and Encryption
All data in transit and at rest needs to be encrypted. Sherdil Cloud has data loss prevention (DLP) policies and cloud-native encryption features that protect sensitive data even if intercepted.
5.Continuous Monitoring and Analytics
Zero Trust feeds on visibility. Ongoing telemetry, logging, and AI-facilitated analytics pick up on anomalous patterns and react automatically to emerging threats. With AWS CloudTrail, Azure Sentinel, and Google Chronicle, we maintain constant visibility.omalous patterns and react automatically to emerging threats. With AWS CloudTrail, Azure Sentinel, and Google Chronicle, we maintain constant visibility.
How Sherdil Cloud Implements Zero Trust
In Sherdil Cloud, we do not view Zero Trust as an inflexible best practice but rather as a path of maturity, incrementally adding security controls to the organization’s cloud platform. Our roadmap for implementation generally features:
-Assessment and Discovery: Discover assets, users, and data flows.
-Policy Definition: Define who can access what, when, and under what conditions.
-Identity Strengthening: Combine centralized IAM with MFA and adaptive access policies.
-Micro-Segmentation Setup: Establish secure zones across cloud workloads.
-Automation and Orchestration: Automate the detection and remediation of threats.
-Continuous Optimization: Periodic audit and optimization of policies to keep up with new threats.
This systematic process maximizes security benefits while minimizing disruption to operations in moving from legacy architecture to Zero Trust.
Benefits of Zero Trust in the Cloud
1.Robust Data Protection
Through enforcing access controls at all levels, Zero Trust makes sure that sensitive information whether customer data, intellectual property, or financial data is kept secure even when credentials are stolen.
2.Less Attack Surface
Micro-segmentation restricts how far attackers can get inside your environment, greatly minimizing breach impact.
3.Compliance and Audit Readiness
Zero Trust fits in with regulatory models such as GDPR, ISO 27001, and HIPAA, streamlining audit processes via rigorous identity confirmation and logging.
4.Greater Visibility and Control
Real-time monitoring and analytics provide complete visibility into each access attempt, allowing for easier detection of insider threats or suspicious behavior.
5.Greater Business Agility
Cloud-native Zero Trust enables secure access from anywhere, empowering distributed teams without compromising security.
Real-World Example: Zero Trust in Action
One of our business customers, a global retail company, was experiencing escalating cloud security breaches as a result of sophisticated access management and remote workforce issues. Sherdil Cloud implemented a Zero Trust architecture across their AWS and Azure environments by:
-Deploying centralized IAM with adaptive MFA.
-Applying device posture validation prior to granting access.
-Implementing network segmentation policies for production and dev environments.
-Integrating AI-powered monitoring for ongoing threat detection.
The outcomes were revolutionary:
-80% decrease in unauthorized access attempts.
-50% shorter incident response time through automated notification.
-Improved compliance posture for data protection laws.
-By implementing Zero Trust, the client gained a balance between easy cloud access and enterprise-level security.
Overcoming Challenges in Zero Trust Adoption
While the benefits are clear, implementing Zero Trust can pose challenges from cultural resistance to technical complexity. Common hurdles include:
| Challenge | Sherdil Cloud Solution |
|---|---|
| Complexity of integration | Phased, modular deployment using automation |
| Legacy system compatibility | Hybrid Zero Trust strategy combining on-prem and cloud |
| User friction due to MFA | Adaptive authentication based on behavior |
| Monitoring overhead | AI-driven analytics for real-time visibility |
Our approach ensures organizations can adopt Zero Trust without sacrificing operational efficiency.
Looking Ahead: The Future of Zero Trust
With AI, IoT, and edge computing transforming business ecosystems, Zero Trust will expand to address new aspects of digital security. We can anticipate the development of Zero Trust AI systems, autonomous threat protection, and cloud-native policy engines that evolve in real-time.
At Sherdil Cloud, we’re already using machine learning–based anomaly detection and context-aware access control in our Zero Trust deployments building smart defenses that learn and adapt in lockstep with the changing threat landscape.
In Conclusion
Zero Trust Architecture is the start of a new era of cloud security, in which trust is no longer presumed but constantly validated. For organizations attempting to protect today’s distributed environments, Zero Trust is not a choice, it is a requirement. Sherdil Cloud assists enterprises in architecting, deploying, and managing Zero Trust systems that integrate protection, flexibility, and innovation, so your cloud can be as dynamic and resilient as your company.
Secure smarter. Operate confidently. Scale with trust with Sherdil Cloud.